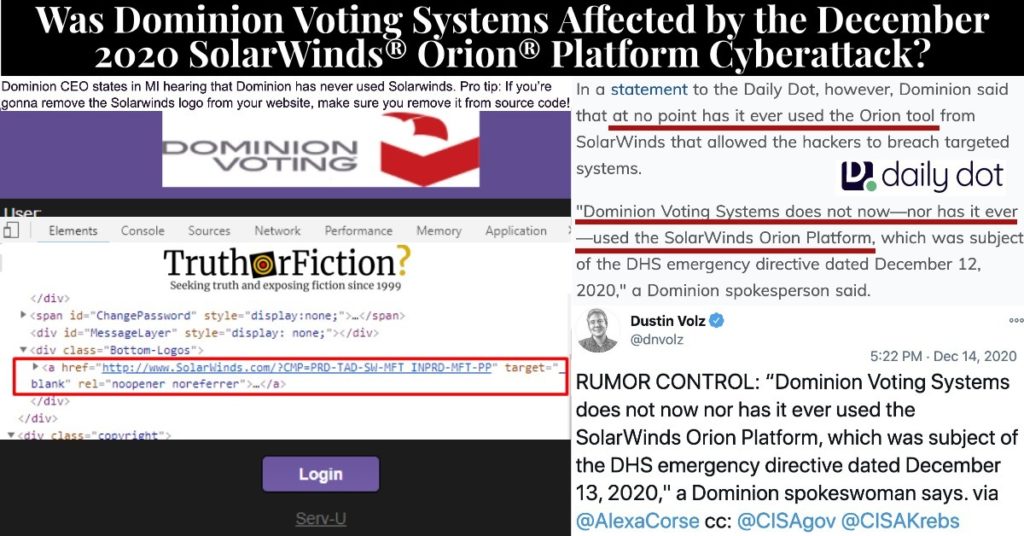
On December 15 2020, a popular post was shared to the far-right forum TheDonald.win. Its topic was included in its title, “Dominion CEO states in MI hearing that Dominion has never used Solarwinds. Pro tip: If you’re gonna remove the Solarwinds logo from your website, make sure you remove it from source code,” and it included a screenshot of a purported Dominion Voting Systems page:

No link was included in the original post, but the image used a red box to highlight source code on a page labeled “Dominion Voting,” directed to SolarWinds.com. The claim was shared with a nearly identical title on Reddit’s r/conspiracy, and was shared by Twitter user @CodeMonkeyZ, who is also QAnon conspiracy pusher and “expert witness” Ron Watkins:
His most influential campaign has been his attempts to smear Dominion Voting Systems. Earlier this month, Watkins posted a video of a Dominion employee using one of the company’s voting machines, falsely claiming the employee was manipulating results. As a result, the 20-year-old employee received death threats and someone hung a noose outside his house.
But such incidents didn’t stop Watkins from becoming a star in the alternate universe that sprouted up to support Trump’s wild allegations of widespread vote-rigging.
Watkins — who lives in Japan — has shown no sign of losing interest in pushing disinformation about the American elections:
What Is SolarWinds, Anyway?
SolarWinds is an information technology company providing enterprise software and products:
SolarWinds Inc. is an American company that develops software for businesses to help manage their networks, systems, and information technology infrastructure. SolarWinds is headquartered in Austin, Texas, with sales and product development offices in a number of locations in the United States and several other countries around the world. The company was publicly traded from May 2009 until the end of 2015, and again from October 2018. It has also acquired a number of companies, some of which it still operates under their original brand names including Pingdom, Papertrail, and Loggly.
‘Dominion CEO States in MI Hearing that Dominion Has Never Used Solarwinds’
On December 15 2020, Michigan’s WWMT published an article (“Dominion CEO says company targeted in ‘reckless disinformation campaign at hearing”) reporting that Dominion Voting Systems chief executive officer John Poulos testified to Michigan lawmakers on that date; however, SolarWinds was not mentioned:
The CEO of Dominion Voting Systems, which provides voting equipment for the majority of Michigan’s counties, testified before the Senate Oversight Committee on Tuesday afternoon [December 15 2020], where he shut down conspiracy theories and allegations that his company had been involved in voter fraud.
The allegations range from conspiracies that Dominion had changed votes, received money funneled through Swiss bank accounts from other countries, and even the claim that the company has ties to the late Venezuelan President Hugo Chavez, who died in 2013.
Dominion Voting Systems CEO John Poulos testified under oath in front of state lawmakers [on December 15 2020] that all of the claims are false and that his company had been the target of a “dangerous and reckless disinformation campaign.”
Detroit News also reported on Poulos’ testimony, but did not mention SolarWinds:
Poulos discredited a plethora of conspiracy theories about his Denver-based company as he appeared under oath before the Senate Oversight Committee.
“We have yet to see our critics make their allegations under oath as I am doing here today,” he told lawmakers.
[…]
“It is technologically impossible to see votes being counted in real-time or to flip them,” he said. “The comments about our company being started in Venezuela with Cuban money with the intent to steal elections are beyond bizarre and are complete lies.”
We did locate a December 15 2020 report by tech news site The Daily Dot, in which a Dominion Voting Systems representative (not Poulos) addressed the rumors about Dominion and the SolarWinds vulnerability:
The screenshot was immediately picked up by far-right outlets such as the Gateway Pundit and was cited by supporters of the president as the latest evidence of voter fraud.
In a statement to the Daily Dot, however, Dominion said that at no point has it ever used the Orion tool from SolarWinds that allowed the hackers to breach targeted systems.
“Dominion Voting Systems does not now—nor has it ever—used the SolarWinds Orion Platform, which was subject of the DHS emergency directive dated December 12, 2020,” a Dominion spokesperson said.
SolarWinds declined to provide a comment to the Daily Dot on the matter given the ongoing investigation into the breach.
Note that the statement was specific in relation to the rumors claiming that Poulos said Dominion “has never used Solarwinds.” In the statement, a Dominion representative said Dominion Voting Systems “does not now—nor has it ever—used the SolarWinds Orion Platform.”
Replicating the Source Code in the Dominion/SolarWinds Screenshot
Based on comments in social media discourse, we were able to locate the page in question: https://dvsfileshare.dominionvoting.com/Web%20Client/Mobile/MLogin.htm.
Viewing source code for the DominionVoting.com page in question did (as of December 16 2020) display “http://www.solarwinds.com/?CMP=PRD-TAD-SW-MFT_INPRD-MFT-PP.” That page was archived here.
When the URL on dominionvoting.com was accessed, the tab was labeled “Serv-U,” a specific SolarWinds product described as “[s]imple, affordable, easy-to-use FTP [file transfer protocol] server software.”
SolarWinds Orion Platform Compromised in December 2020
On December 14 2020, KrebsOnSecurity.com reported:
Communications at the U.S. Treasury and Commerce Departments were reportedly compromised by a supply chain attack on SolarWinds, a security vendor that helps the federal government and a range of Fortune 500 companies monitor the health of their IT networks. Given the breadth of the company’s customer base, experts say the incident may be just the first of many such disclosures.
[…]
In a security advisory, Austin, Texas based SolarWinds acknowledged its systems “experienced a highly sophisticated, manual supply chain attack on SolarWinds Orion Platform software builds for versions 2019.4 HF 5 through 2020.2.1, released between March 2020 and June 2020.”
SolarWinds’ Security Advisory
On SolarWinds.com, a “security advisory” dated “Recent as of December 16, 2020, 9:30am CST” explained:
SolarWinds has been made aware of a cyberattack to our systems that inserted a vulnerability within our SolarWinds® Orion® Platform software builds for versions 2019.4 HF 5, 2020.2 with no hotfix installed, and 2020.2 HF 1, which, if present and activated, could potentially allow an attacker to compromise the server on which the Orion products run. We have been advised that this incident was likely the result of a highly sophisticated, targeted, and manual supply chain attack by an outside nation state, but we have not independently verified the identity of the attacker.
[…]
Based on our investigation, we are not aware that this vulnerability affects other versions—including future versions—of Orion Platform products. We have scanned the code of all our software products for markers similar to those used in the attack on our Orion Platform products identified above, and we have found no evidence that other versions of our Orion Platform products or our other products or agents contain those markers. As such, we are not aware that other versions of Orion Platform products have been impacted by this security vulnerability. Other non-Orion Platform products are also not known by us to be impacted by this security vulnerability.
SolarWinds also listed “known affected products,” as well as “SolarWinds products believed to be NOT AFFECTED by this security vulnerability.” Products believed to be not affected included:
- Serv-U FTP Server
- Serv-U Gateway
- Serv-U MFT Server
Summary
A steady stream of post-election disinformation included a December 15 2020 rumor that Dominion Voting Systems was compromised as part of a SolarWinds’ Orion platform security alert. Those who clicked a link attached to a screenshot of a login page on dominionvoting.com would find a “solarwinds.com” link in the source code of a page titled “Serv-U.” A Dominion Voting Systems representative told The Daily Dot that the company did not at any point utilize SolarWinds’ Orion platform; Dominion appeared to use a SolarWinds FTP called “Serv-U.” Per SolarWinds’ most recent update after the vulnerability was identified, Serv-U was not among products affected by the breach.
- Dominion CEO states in MI hearing that Dominion has never used Solarwinds. Pro tip: If you’re gonna remove the Solarwinds logo from your website, make sure you remove it from source code!
- Dominion CEO states in MI hearing that Dominion has never used Solarwinds. Pro tip: If youâre gonna remove the Solarwinds logo from your website, make sure you remove it from source code!
- Dominion Voting Systems uses SolarWinds products and it is still not powered down. Was Dominion Voting Systems a target? Was Dominion Voting Systems hacked?
- SolarWinds
- Dominion CEO says company targeted in 'reckless disinformation campaign at hearing
- Dominion Voting CEO: 'Disinformation campaign' defies logic
- How the SolarWinds hack became the new focus of election fraud conspiracies
- Dominion SolarWinds Source Code
- Dominion SolarWinds Source Code
- Dominion SolarWinds Serv-U
- U.S. Treasury, Commerce Depts. Hacked Through SolarWinds Compromise
- SolarWinds Orion/Serv-U | Security Advisory