In March 2020, as global fears about the COVID-19 pandemic continued to grow among a morass of disinformation and state-sponsored propaganda, security experts warned about websites using their fear of the novel coronavirus to infect their machines and subject them to information theft.
According to the cybersecurity company Malwarebytes:
Cybercriminals targeted users in Japan with an Emotet campaign that included malicious Word documents that allegedly contained information about coronavirus prevention. Malware embedded into PDFs, MP4s, and Docx files circulated online, bearing titles that alluded to protection tips. Phishing emails that allegedly came from the US Centers for Disease Control and Prevention (CDC) were spotted, too. Malwarebytes also found a novel scam purporting to direct users to a donation page to help support government and medical research.
All of these threats rely on the same dangerous intersection of misinformation and panic—a classic and grotesque cybercrime tactic. A great defense to these is, quite simply, the truth.
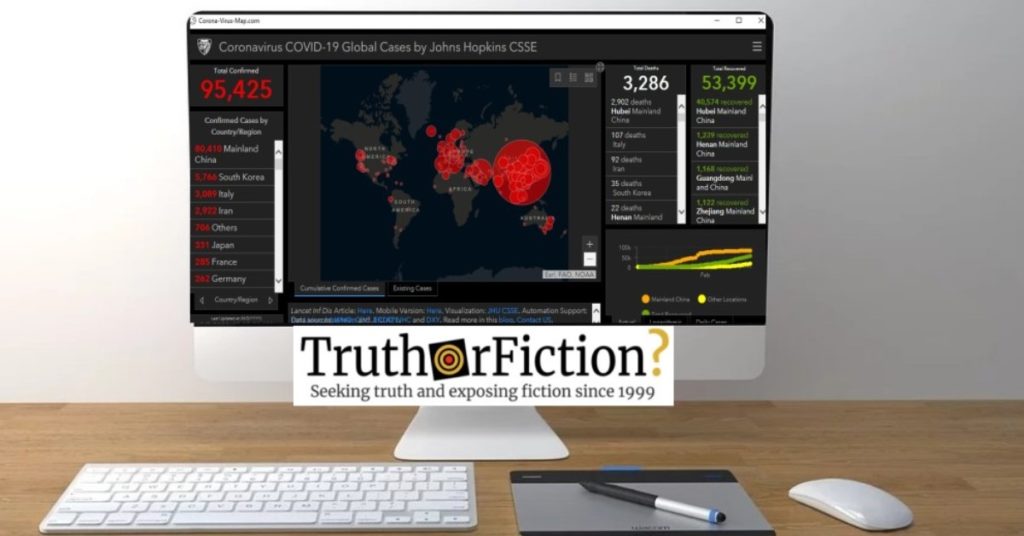
The company also identified one site, “coronavirusmap.com,” that presented itself as a source of information for tracking cases of the epidemic around the globe:
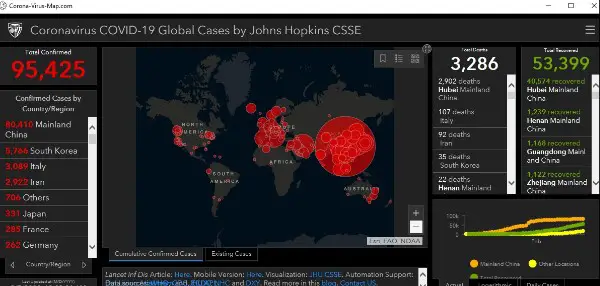
But in reality, the site hit users with a variant of the spyware known as AzorUlt, which steals information while also allowing other harmful programs to enter machines.
The tech news site SC Magazine further reported that the spyware hidden within the site “can also take unauthorized screenshots, resolved and save a victim’s public IP address, and gather information on infect machines, including the OS system, architecture, hostname and username.”
Shai Alfasi, a researcher for another security company, Reason Labs, told the magazine that “coronavirusmap” did not rely on email or phishing tactics to spread. “As the coronavirus continues to spread and more apps and technologies are developed to monitor it, we will likely be seeing an increase in corona malware and corona malware variants well into the foreseeable future,” he added.
In his own post detailing the nature of this latest attack, Alfasi said that the AzorUlt spyware is “commonly sold on Russian underground forums.”
- Battling Online Coronavirus Scams With Facts
- Malicious Coronavirus Map Hides AZORult Info-Stealing Malware
- COVID-19, Info Stealer & the Map of Threats – Threat Analysis Report
- Coronavirus Goes Cyber With Emotet
- Coronavirus Used to Spread Malware Online
- CyberheistNews Vol 10 #6 [Heads-Up] Scam of the Week: Coronavirus Phishing Attacks in the Wild